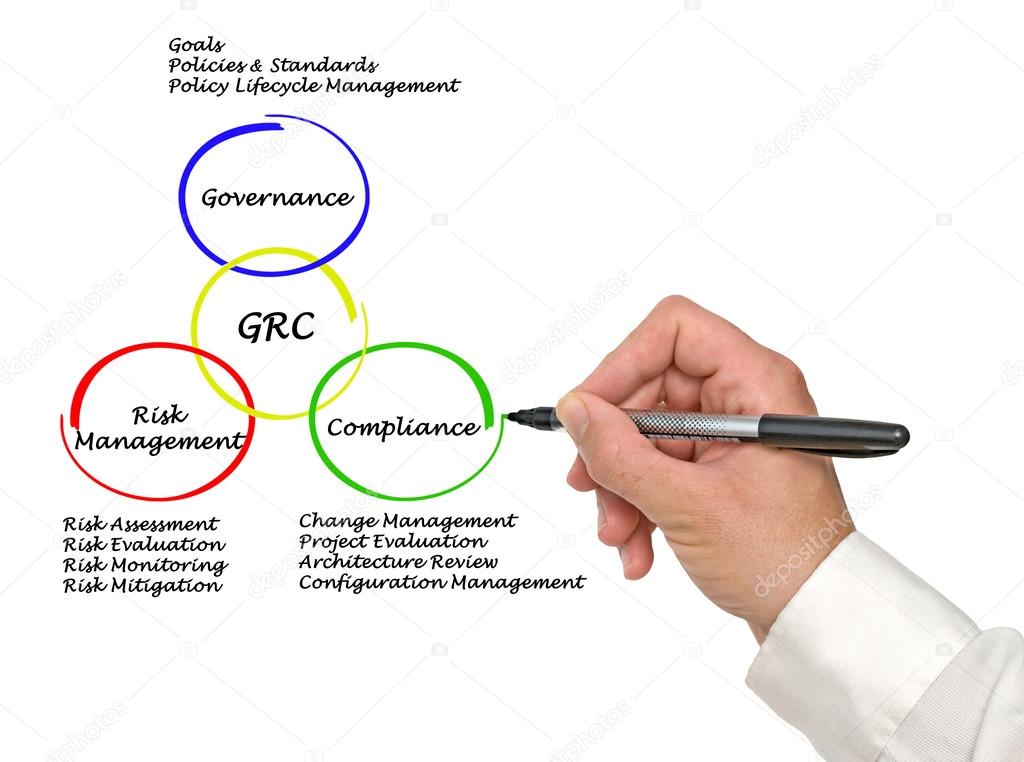
Governance, Risk, & Compliance (GRC)
Does your industry require a GRC strategy by law? Truth is, most don’t despite the increasing need to reduce the threats & vulnerabilities in the digital era. Implementing policies & procedures for GRC will significantly improve your Cyber Security efforts & help to prevent Cyber Attacks. Schedule a Consultation for a more personalized & in-depth analysis of your Governance, Risk, & Compliance!

Governance
Governance is the act of ensuring that organizational activities are aligned in a way that supports the organization’s business goals & reduces the threats involved.

Risk Management
Risk Management is the process of understanding and prioritizing risks within the business that reduces the likelihood of threats & vulnerabilities.

Compliance
Compliance is making sure that the business activities are operated in a way that meets the laws & regulations impacting those systems within your industry.
Top 6 Cyber Security Risks
There are dozens of ways malicious actors attempt to steal, corrupt, & hold data for ransom. With so many risks & threats, being diligent in the protection of your data is critical now more than ever. Here are the Top 6 Cyber Security Risks you need to know:
1. Session Riding
This vulnerability is caused by weaknesses that allow an attacker to force a user to submit a malicious request without their knowledge when the user is authenticated to the website. The site will have no way to distinguish between a forged request sent by the victim and a legitimate request sent by the victim. This is to cause a state change on the server, such as changing the victim’s password, and using the access to steal data or install ransomware.
2. Spoofing
This vulnerability is caused by weaknesses that allow the website to accept invalid data. An attacker could send scripts to fool the web server to produce usernames, passwords, or entire customer databases. The attacker could also spoof the content on the website and redirect traffic to an attacker-controlled site and steal user credentials or install malware or ransomware.
3. Click Jacking
This vulnerability is caused by weaknesses that allow an attacker to insert stylesheets, iframes, text boxes, or layers and “hijack” a web page or portions of a web page to trick users and steal user credentials or account secrets for easy intrusion to install malware or ransomware.
4. Sniffing
This vulnerability is caused by weaknesses that do not force encryption and instead allow the transmission of sensitive or security-critical data in cleartext. The attacker can easily discover and steal with simple network sniffing and can use it to make intrusion or move laterally once inside to eventually exfiltrate data or infect ransomware.
5. Phishing
This weakness is caused when a user unknowingly clicks an email attachment that is embedded with malicious malware with the intention to compromise your system or data.
6. DDOS Attacks
This weakness is caused when an attacker or group of attackers deliberately send an enormous amount of requests to the server with the intention to cause it to shut down.
Contact us or follow us for prevention methods you can take to reduce your Cyber Security Risks.
Governance, Risk, & Compliance is the practices & procedures that reduce Cyber Security threats & vulnerabilities. Learn more about GRC in this article.
How do you reduce your Cyber Security threats & vulnerabilities to reasonable levels? Read the full article on IT Security 101: The Basics of Risk Management here.
Want to know more about preventing Cyber Attacks? Check out our free & ongoing webinar series: Cyber Hygiene 101. Register today, everyone is welcome!
Schedule a Governance, Risk, & Compliance Analysis
Whether your industry requires a GRC strategy or not, OQP Solutions can help you craft a plan that helps you reduce the risks of Cyber Attacks in your organization. From the IT infrastructure to the Security Awareness Trainings, managing your company’s policies & procedures for protection is critical to your future success. Contact us for more information or schedule an analysis today!